 If you receive an error similar to below when calling the GCP API using ADC login credentials with either gcloud or terraform:
If you receive an error similar to below when calling the GCP API using ADC login credentials with either gcloud or terraform:
Cannot add the project "myproj-i1wsbbn8pkfeq3jhkcg0z4" to ADC as the quota project because the account in ADC does not have the "serviceusage.services.use" permission on this project. You might receive a "quota_exceeded" or "API not enabled" error.
The problem is that a valid quota project is not specified in the local ADC credentials file. Either:
- The ADC credentials have an empty or invalid quota project
- The quota project does not have the Cloud Resource Manager API enabled
- Your user does not have the “Server Usage Admin” role
ADC Credentials have empty or invalid quota project
The local ADC credentials file needs a ‘quota_project_id’ field. Use the grep below to see if it exists.
# will be empty if quota project not defined for ADC grep quota_project_id ~/.config/gcloud/application_default_credentials.json
If it is empty or uses an invalid/deleted project id, you can fix it without needing to reauthenticate.
# show list of valid project id gcloud projects list --format="csv[no-heading](project_id)" # update ADC file with valid project id gcloud auth application-default set-quota-project <my-quota-project-id>
But the root cause for the ADC file not having a valid quota project is because the ADC defaults to using the main gcloud config values, so you should define the value there for future usage.
# ADC will use the quota project in gcloud as the first fallback gcloud config set billing/quota_project <my-quota-project-id> # ADC will use default project as last fallback gcloud config set project <my-quota-project-id>
Quota Project needs Cloud Resources Manager API enabled
The quota project also needs the Cloud Resources Manager API enabled.
# is required API enabled? gcloud services list --project <my-quota-project-id> | grep cloudresourcemanager.googleapis.com # if not, enable gcloud services enable cloudresourcemanager.googleapis.com --project <my-quota-project-id>
Your user does not have Service Usage Admin role
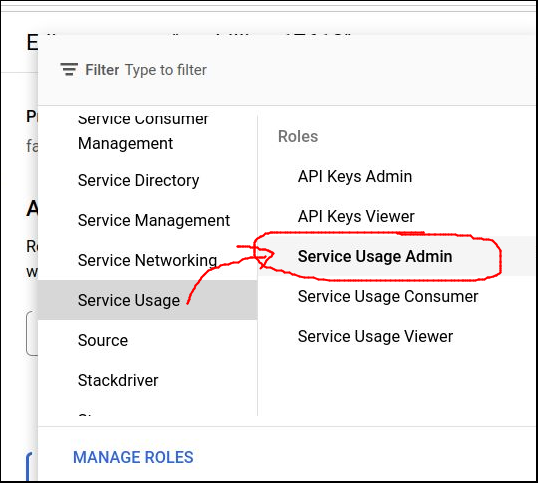
Your ADC user needs to have the “Service Usage Admin” role (roles/serviceusage.serviceUsageAdmin). This should be set at either the quota project level OR organization level (depending on your user implementation). If your user is Owner/Editor, you already have this permission.
Go to IAM & Admin > IAM, select your user and grant the “Service Usage Admin” role as shown below. You may need to have your GCP administrator add this role.
REFERENCE
Google ref, gcloud auth application-default set-quota-project
Google ref, Application Default Credentials
Google ref, troubleshooting ADC talks about quota project
Google ref, gcloud auth application-default login
Github hashicorp issue, lists breaking change in 2020 that requires quota project
Google release notes, lists breaking change with ADC and quota project
artcoded.net, details how user needs “Service Usage Admin” role when hitting this error
GCP, “Service Usage Admin” role
GCP, Understanding roles “Service Usage Admin”
NOTES
If this is your absolute first project, you can use the Google console web UI to create a project that can specifically be used as the quota project.
Link to enabling Cloud Resource Manager API
https://console.developers.google.com/apis/api/cloudresourcemanager.googleapis.com/overview?project=my-project-id-123
Specifying quota project as parameter
gcloud auth application-default login --project <my-quota-project-id>