 GitLab Pipelines provide the ability to define a build workflow, and for projects that are building an OCI (Docker) image, there is a convenient method for doing container security scanning as part of the build process.
GitLab Pipelines provide the ability to define a build workflow, and for projects that are building an OCI (Docker) image, there is a convenient method for doing container security scanning as part of the build process.
Include Container Scanning
As described in the official documentation, add the following include to your .gitlab-ci.yml pipeline definition.
include: - template: Jobs/Container-Scanning.gitlab-ci.yml
Customize Analyzer behavior
Then customize the scanning behavior by specifying the exact image/tag you want to scan and any parameters. Using a job id named ‘container_scanning’ allows you to override the default definition and define the expected ‘CS_IMAGE’ based on your own custom logic.
# override scanning definition
container_scanning:
before_script: |
VERSION=${CI_COMMIT_TAG#v}
export CS_IMAGE=${CI_REGISTRY_IMAGE}:${VERSION}
variables:
GIT_STRATEGY: fetch # ensure access to Dockerfile
CS_DISABLE_LANGUAGE_VULNERABILITY_SCAN: "false" # scan non-OS packages as well
In my particular case, I am defining the version based on a git tag that looks like “v<major>.<minor>.<patch>”, and use the before_script section to parse out that value and set the CS_IMAGE variable expected by the scanner.
I also set custom values for the GIT_STRATEGY and CS_DISABLE_LANGUAGE_VULNERABILITY_SCAN which customize the scanning behavior.
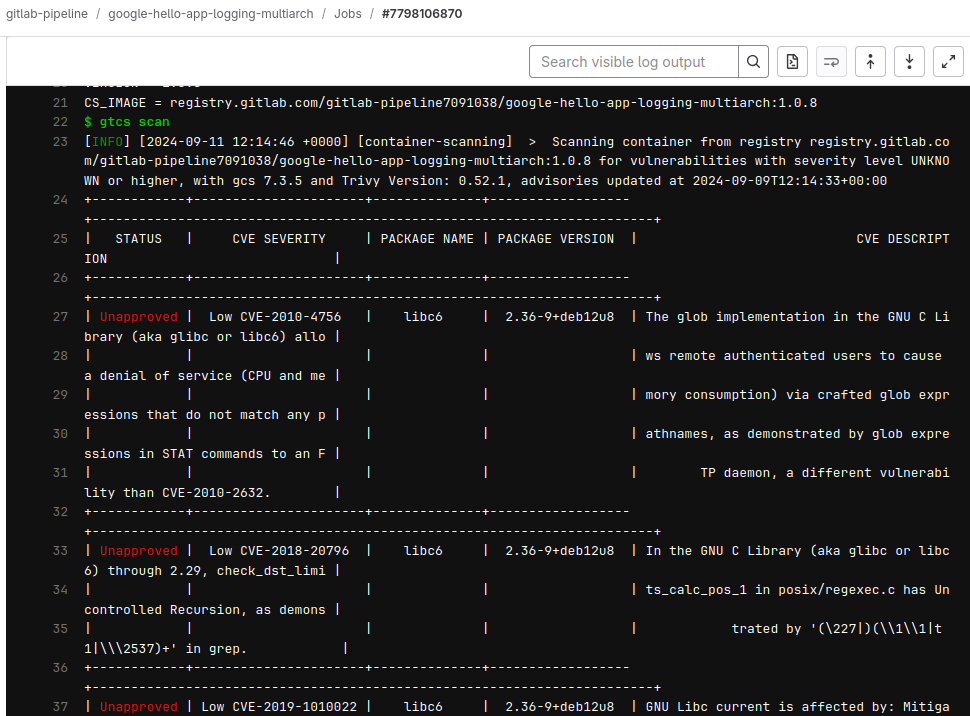
Scanning report
You will now see an additional ‘container_scanning’ job in your pipeline, and viewing the output, you can see the Trivy report of any vulnerabilities discovered.
REFERENCES
GitLab docs, container security scanning