 The Meltdown vulnerability affects Intel and some ARM (but not AMD) processor chips and can allow unprivileged access to memory in the kernel and other processes. Canonical has committed to kernel patches to address this issue by January 9, 2018.
The Meltdown vulnerability affects Intel and some ARM (but not AMD) processor chips and can allow unprivileged access to memory in the kernel and other processes. Canonical has committed to kernel patches to address this issue by January 9, 2018.
If you need to check your system, or perhaps have already patched your systems but want to verify that the issue truly is resolved, there is a proof of concept available on github that exercises a rogue data cache load (Variant 3).
In this article I will show you how to compile and run this non-destructive C++ program on Ubuntu 14.04 and 16.04.
Note that you should be extremely diligent when running any executable on your system, especially one that exercises a known vulnerability. If you see logic in the code that cannot be trusted, then do not compile it.
Download and compile
The first step is to download the C++ project that will exercise the vulnerability. You can grab it from github and compile it using:
$ sudo apt-get install git make build-essential $ git clone https://github.com/raphaelsc/Am-I-affected-by-Meltdown.git $ cd Am-I-affected-by-Meltdown $ make
A ‘meltdown-checker’ executable file has now been created in the current directory.
Allow kernel symbols to be read
Running the meltdown checker at this point will more than likely cause a core dump because applications by default cannot read kernel symbols.
$ ./meltdown-checker Unable to read /proc/kallsyms. That means your system doesn't allow non-root or any program to read the file. Your options are either running the program as root *OR* setting /proc/sys/kernel/kptr_restrict to 0, as follow: sudo sh -c "echo 0 > /proc/sys/kernel/kptr_restrict" Aborted (core dumped)
These default permissions are seen as an extra layer of defense, but we will need to disable it in order to allow the POC to check whether the address of a system call found by exploiting Meltdown matches the system call table.
This can be done using the following command:
$ sudo sh -c "echo 0 > /proc/sys/kernel/kptr_restrict"
Run vulnerability check
This vulnerability is centered around accessing kernel memory from userspace. Run the POC by executing:
./meltdown-checker
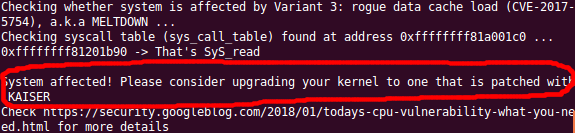
And if your system is vulnerable, you will see output like the screenshot below.
REFERENCES
https://googleprojectzero.blogspot.com/2018/01/reading-privileged-memory-with-side.html
https://cyber.wtf/2017/07/28/negative-result-reading-kernel-memory-from-user-mode/
https://github.com/raphaelsc/Am-I-affected-by-Meltdown (poc code)
https://meltdownattack.com/meltdown.pdf (whitepaper)
https://www.amd.com/en/corporate/speculative-execution (AMD response)
https://insights.ubuntu.com/2018/01/04/ubuntu-updates-for-the-meltdown-spectre-vulnerabilities/
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SpectreAndMeltdown (Ubuntu response)
https://en.wikipedia.org/wiki/Meltdown_(security_vulnerability)
https://github.com/IAIK/KAISER (KAISER patch for linux to avoid side channels)
https://en.wikipedia.org/wiki/Kernel_page-table_isolation (describes kernel page table isolation patch)
https://arstechnica.com/gadgets/2018/01/whats-behind-the-intel-design-flaw-forcing-numerous-patches/ (KAISER discussion on performance affect)