 The Meltdown vulnerability affects Intel and some ARM (but not AMD) processor chips and can allow unprivileged access to memory in the kernel and other processes.
The Meltdown vulnerability affects Intel and some ARM (but not AMD) processor chips and can allow unprivileged access to memory in the kernel and other processes.
Canonical has committed to kernel patches to address this issue by January 9, 2018 and the first candidate kernel patches have now been released for Xenial and Trusty LTS.
UPDATE Jan 11 2018: The main Ubuntu repositories now have the official patches. Read my article here for more information.
In this article, I’ll step through patching an Ubuntu 16.04 kernel with the candidate kernel fixes.
Specifically, I’m going to use VirtualBox and a Xenial64 vagrant box, but feel free to use any host running Ubuntu 16.04 Xenial for these steps.
If you want to use my Vagrant files, grab them here. Else go through the instructions below.
Determine current kernel version
First, we want to take note of the current kernel version. This is easily done using the following command:
$ uname -r 4.4.0-104-generic
If you are running Ubuntu 16.04 with the latest updates you will probably have “4.4.0-104-generic”, which is known to be vulnerable to Meltdown.
Verify vulnerability
In a previous article I detailed how to run the Meltdown POC that checks if your system is vulnerable. See that article for full details, but let me lay out the essential steps here, and watch how the output changes after we update the kernel.
Download and compile the POC:
$ sudo apt-get install git build-essential $ git clone https://github.com/raphaelsc/Am-I-affected-by-Meltdown.git $ cd Am-I-affected-by-Meltdown $ make
Allow the program to read the kernel symbols, which is necessary to allow the POC to check whether the address of a system call found by exploiting Meltdown matches the system call table.
$ sudo sh -c "echo 0 > /proc/sys/kernel/kptr_restrict"
Then run the proof of concept:
$ ./meltdown-checker
On an unpatched system such as this, you will receive output similar to below saying ‘System affected!’
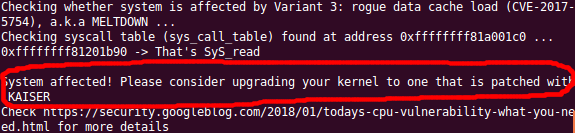
Add candidate kernel PPA
As linked on Ubuntu’s KB page for Spectre and Meltdown, there are now candidate kernels available if you use the PTI PPA. The “4.4.0-109-generic” kernel released on Jan 07 2018 is the one we want to use on our Xenial installation.
$ sudo add-apt-repository ppa:canonical-kernel-team/pti -y $ sudo apt-get update
Install candidate kernels
Now we can check for the availability of the 4.4.0-109 packages:
$ sudo apt-cache search linux-headers-4.4.0-109-generic $ sudo apt-cache search linux-image-4.4.0-109-generic
And then install the header and image packages.
$ sudo apt-get install linux-headers-4.4.0-109-generic linux-image-4.4.0-109-generic -y
And finally, reboot to make the kernel changes take affect:
$ sudo init 6
After reboot, you should now see a new kernel version reported.
$ uname -r 4.4.0-109-generic
Validate mitigation of vulnerability
The last step is to run the Meltdown POC program again, and verify that the system is not affected anymore.
The application will once again need to be given permission to read kernel symbols, then the POC can be run once again.
$ sudo sh -c "echo 0 > /proc/sys/kernel/kptr_restrict" $ ./meltdown-checker
You should now get output similar to below that indicates the ‘System not affected’.
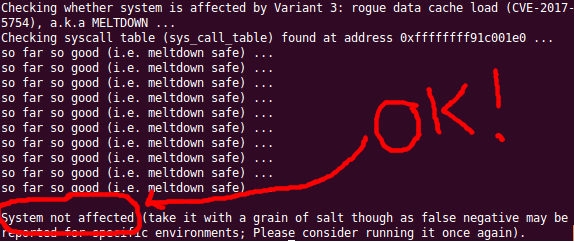
REFERENCES
https://googleprojectzero.blogspot.com/2018/01/reading-privileged-memory-with-side.html
https://github.com/raphaelsc/Am-I-affected-by-Meltdown (poc code)
https://meltdownattack.com/meltdown.pdf (whitepaper)
https://www.amd.com/en/corporate/speculative-execution (AMD response)
https://insights.ubuntu.com/2018/01/04/ubuntu-updates-for-the-meltdown-spectre-vulnerabilities/
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SpectreAndMeltdown (Ubuntu response)
https://en.wikipedia.org/wiki/Meltdown_(security_vulnerability)
https://en.wikipedia.org/wiki/Kernel_page-table_isolation (describes kernel page table isolation patch)