 The Meltdown vulnerability affects Intel and some ARM (but not AMD) processor chips and can allow unprivileged access to memory in the kernel and other processes. Canonical has committed to kernel patches to address this issue by January 9, 2018.
The Meltdown vulnerability affects Intel and some ARM (but not AMD) processor chips and can allow unprivileged access to memory in the kernel and other processes. Canonical has committed to kernel patches to address this issue by January 9, 2018.
A paper coming out of Graz University of Technology in Austria and written by Daniel Gruss, Moritz Lipp, Michael Schwarz, Richard Fellner, Clementine Maurice, and Stefan Mangard provides a patched 4.10.0 kernel that isolates the kernel address space and resolves CVE-2017-5754 (Meltdown).
No one is advocating this as the fix for your production instances, but if you want to play around with this patched kernel in a virtualized environment, I’ll lead you through the steps in this article.
UPDATE Jan 11 2018: The main Ubuntu repositories now have the official patches. Read my article here for more information.
Determine current kernel version
First, we want to take note of the current kernel version. This is easily done using the following command:
$ uname -r 4.4.0-104-generic
In my case, where I am using VirtualBox and the ‘ubuntu/xenial64’ vagrant box version ‘20180105.0.0’, and the kernel is ‘4.4.0-104-generic’ as shown above.
Install 4.10 kernel with patch
While the researcher’s github page has patched source I could use to patch the standard linux kernel source, they also provide precompiled .deb files which will make it more convenient for our purposes.
Download the image and headers packages from the dist directory of their github project:
$ wget https://github.com/IAIK/KAISER/blob/master/dist/linux-headers-4.10.0-rc6-kaiser_4.10.0-rc6-kaiser-2_amd64.deb?raw=true -O linux-headers-4.10.0-rc6-kaiser_4.10.0-rc6-kaiser-2_amd64.deb $ wget https://github.com/IAIK/KAISER/blob/master/dist/linux-image-4.10.0-rc6-kaiser_4.10.0-rc6-kaiser-2_amd64.deb?raw=true -O linux-image-4.10.0-rc6-kaiser_4.10.0-rc6-kaiser-2_amd64.deb
Install the linux-headers package:
$ dpkg -i linux-headers-4.10.0-rc6-kaiser_4.10.0-rc6-kaiser-2_amd64.deb Selecting previously unselected package linux-headers-4.10.0-rc6-kaiser. (Reading database ... 59094 files and directories currently installed.) Preparing to unpack linux-headers-4.10.0-rc6-kaiser_4.10.0-rc6-kaiser-2_amd64.deb ... Unpacking linux-headers-4.10.0-rc6-kaiser (4.10.0-rc6-kaiser-2) ... Setting up linux-headers-4.10.0-rc6-kaiser (4.10.0-rc6-kaiser-2) ...
And then install the linux-image package:
$ dpkg -i linux-image-4.10.0-rc6-kaiser_4.10.0-rc6-kaiser-2_amd64.deb Selecting previously unselected package linux-image-4.10.0-rc6-kaiser. (Reading database ... 85614 files and directories currently installed.) Preparing to unpack linux-image-4.10.0-rc6-kaiser_4.10.0-rc6-kaiser-2_amd64.deb ... Unpacking linux-image-4.10.0-rc6-kaiser (4.10.0-rc6-kaiser-2) ... Setting up linux-image-4.10.0-rc6-kaiser (4.10.0-rc6-kaiser-2) ... update-initramfs: Generating /boot/initrd.img-4.10.0-rc6-kaiser W: mdadm: /etc/mdadm/mdadm.conf defines no arrays. Generating grub configuration file ... Found linux image: /boot/vmlinuz-4.10.0-rc6-kaiser Found initrd image: /boot/initrd.img-4.10.0-rc6-kaiser Found linux image: /boot/vmlinuz-4.4.0-104-generic Found initrd image: /boot/initrd.img-4.4.0-104-generic done
Reboot the machine to ensure the new kernel is loaded.
$ sudo init 6
Validate new kernel version
Recall that the original linux kernel version was 4.4.0. Now check again:
$ uname -r 4.10.0-rc6-kaiser
Notice the change to ‘4.10.0-rc6-kaiser’.
Run vulnerability check
In my previous article I detailed how to run the Meltdown POC that checks if your system is vulnerable. See that article for full details, but let me lay out the essential steps here, and watch how the output now changes with our patched kernel.
Download and compile the POC:
$ sudo apt-get install git make build-essential $ git clone https://github.com/raphaelsc/Am-I-affected-by-Meltdown.git $ cd Am-I-affected-by-Meltdown $ make
Allow the program to read the kernel symbols, which is necessary to allow the POC to check whether the address of a system call found by exploiting Meltdown matches the system call table.
$ sudo sh -c "echo 0 > /proc/sys/kernel/kptr_restrict"
Then run the proof of concept:
./meltdown-checker
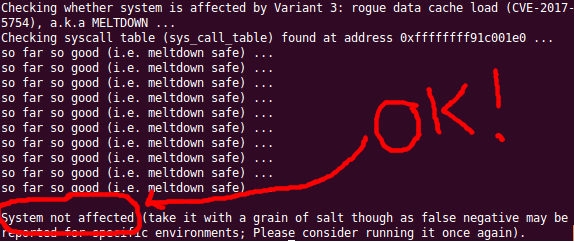
You should get output similar to below that indicates the ‘System not affected’.
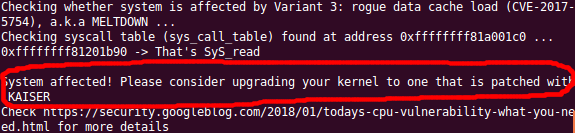
On an unpatched system (as you can recall from my previous article), you would have received output similar to below saying ‘System affected!’
REFERENCES
http://www.businessinsider.com/r-how-a-researcher-hacked-his-own-computer-and-found-worst-chip-flaw-2018-1 (Daniel Gruss story)
https://github.com/IAIK/KAISER (KAISER patch for linux to avoid side channels)
https://googleprojectzero.blogspot.com/2018/01/reading-privileged-memory-with-side.html
https://github.com/raphaelsc/Am-I-affected-by-Meltdown (poc code)
https://meltdownattack.com/meltdown.pdf (whitepaper)
https://www.amd.com/en/corporate/speculative-execution (AMD response)
https://insights.ubuntu.com/2018/01/04/ubuntu-updates-for-the-meltdown-spectre-vulnerabilities/
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SpectreAndMeltdown (Ubuntu response)
https://en.wikipedia.org/wiki/Meltdown_(security_vulnerability)
https://en.wikipedia.org/wiki/Kernel_page-table_isolation (describes kernel page table isolation patch)
https://arstechnica.com/gadgets/2018/01/whats-behind-the-intel-design-flaw-forcing-numerous-patches/ (KAISER discussion on performance affect)