 WinSCP is a Windows application for transferring files via fto or scp to remote host. A feature not many take advantage of is the ability to create automation scripts that can execute these transfers as silent batch jobs.
WinSCP is a Windows application for transferring files via fto or scp to remote host. A feature not many take advantage of is the ability to create automation scripts that can execute these transfers as silent batch jobs.
In this article I will show how to use scripted FTP commands and SCP commands to automate your file transfer jobs.
When dealing with SCP sessions, we need to set a hostkey value in order to meet security concerns, so we will go into detail on how to retrieve and provide that value.
WinSCP.com
After installing WinSCP in the default “c:\program files (x86)\winscp” directory, you will see two executables. winscp.exe is the Windows GUI. winscp.com is the console based program which we will use throughout this article.
FTP smoke test
Let’s run through a quick example of connecting to ftp.ubuntu.com as the anonymous user, changing to the ‘ubuntu’ directory, getting a file listing, downloading a 14Mb file, then disconnecting.
Create a script file named “ftpcmd.txt” containing:
open ftp://anonymous:guest@ftp.ubuntu.com cd ubuntu ls get -transfer=binary ls-lR.gz exit
Drop down the command prompt and run:
"c:\Program Files (x86)\WinSCP\WinSCP.com" "/script=ftpcmd.txt"
You should see a directory list of ftp.ubuntu.com/ubuntu and then a binary file named “ls-lR.gz” will be downloaded using the get command.
For a full list of command available see the winscp script commands.
SCP smoke test
The scp commands used to connect and run commands on a remote host follow the same pattern as the example above. For example (ignoring hostkey for a moment), here is a script for transferring a local file to a remote host in “/tmp” and setting the permissions.
open scp://myuser@Myp4ss@192.168.1.10 put mylocalfile.txt /tmp/myremotefile.txt -transfer=auto chmod 755 /tmp/myremotefile.txt ls /tmp/myremotefile.txt exit
But there is one more thing you need because this is scp – a hostkey to prove this is the remote host you intended.
Host authenticity
Dealing with SCP adds one additional layer of security. Because we are essentially dealing with ssh, we either need to send the hostkey of the remote host (as a security measure to validate authenticity) or circumvent all security and allow all hostkeys (-hostkey=”*”). It is highly recommended that you send the hostkey.
There are multiple ways to fetch the hostkey value, but the easiest is to use the GUI winscp.exe. If you use the GUI to open a session to the remote host, you should get the following message if the key has not already been added to the registry.
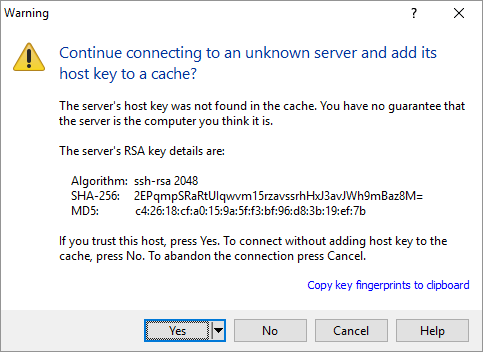
Select “Copy key fingerprints to clipboard”, and then paste it into a text editor like Notepad++. There will be two lines pasted in, both start with the shown “Algorithm” value (e.g. ‘ssh-rsa 2048’).
The first line gives the sha-256 value of the key, the second is the MD5 fingerprint of the value. Either will work work to allow WinSCP.com to establish a session with the remote host.
Append the “-hostkey” switch to the end of the ‘open’ command to inform WinSCP that a host with that key is valid. I’ve used ellipsis to shorten the display below, but you must use the full value.
open scp://myuser@Myp4ss@192.168.1.10 -hostkey="ssh-rsa 2048 2EPqm... 8M="
It does not matter if you use the first or second line, either will prove to WinSCP that the remote host is one that you trust.
If the script name is “scpcmd.txt”, and you have a local file named “mylocalfile.txt” then you can run the command as below.
"c:\Program Files (x86)\WinSCP\WinSCP.com" "/script=scpcmd.txt"
And you should be able to see that the remote file has been transferred and has user/group permissions set to full permissions on the remote host.
REFERENCES
https://winscp.net/eng/docs/commandline
https://winscp.net/eng/docs/scripting#commands
https://winscp.net/eng/docs/faq_script_non_recursive (filemask to avoid recursive sync and avoid subfolders)
https://winscp.net/eng/docs/scripting#arguments (scripting args)
https://winscp.net/eng/docs/ssh_verifying_the_host_key (verifying host key, copy to clipboard)
https://winscp.net/forum/viewtopic.php?t=12526 (wilcard hostkey acceptance)
NOTES
Accepted host keys from GUI saved in registry to: HKCU\Software\Martin Prikryl\WinSCP 2\SshHostKeys
Get algorithm, hostkey
ssh-keyscan <remotehost>
Get fingerprint of hostkey
ssh-keygen -l -E md5 -f <(ssh-keyscan <remoteserver> | grep ssh-ed25519)