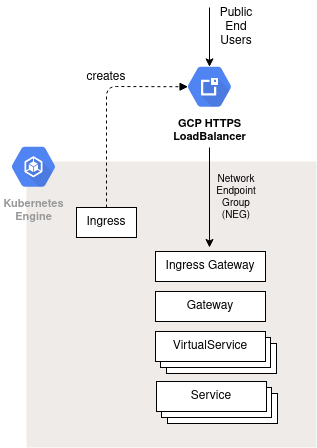
 As opposed to public GKE clusters which have their IP addresses exposed, private GKE clusters use private internal IP addresses. This provides an enhanced security stance, but also means we need a solution such as Anthos Service Mesh to explicitly expose our services.
As opposed to public GKE clusters which have their IP addresses exposed, private GKE clusters use private internal IP addresses. This provides an enhanced security stance, but also means we need a solution such as Anthos Service Mesh to explicitly expose our services.
In our previous article, we built a private GKE cluster using Terraform. In this article, we will extend that and deploy Anthos Service Mesh to expose our cluster services.
Prerequisites
Per my previous article, you should have already installed all the tools necessary to create a private GKE cluster with private endpoint.
Start build
Just like the previous article, start the build process using the menu script.
# pull project from github # git clone https://github.com/fabianlee/gcp-gke-clusters-ingress.git cd gcp-gke-clusters-ingress # show build steps ./menu.sh
Continue build using menu actions
In the previous article, you got as far as creating the private GKE cluster with the “privgke” action.
Continue down the menu actions to install ASM and then a sample app to test our public exposure.
kubeconfig Select KUBECONFIG kubeconfig-ap-pub-10-0-91-0 k8s-register Register with hub and get fleet identity k8s-scale Apply balloon pod to warm up cluster k8s-ASM Install ASM on cluster k8s-certs Create and load TLS certificates k8s-helloapp Install hello apps that will be exposed by LB k8s-lb-tcp Deploy Ingress Gateway and internal TCP LB k8s-lb-https Deploy public and internal HTTPS LB k8s-curl Run curl to test public and private hello endpoints
Select “std-prv-10-0-100-0” for the “kubeconfig” action, since we are working on the private GKE cluster.
It can take 5+ minutes for the GCP HTTPS LB to create itself and be ready for testing, so attempt “k8s-curl” multiple times before assuming failure.
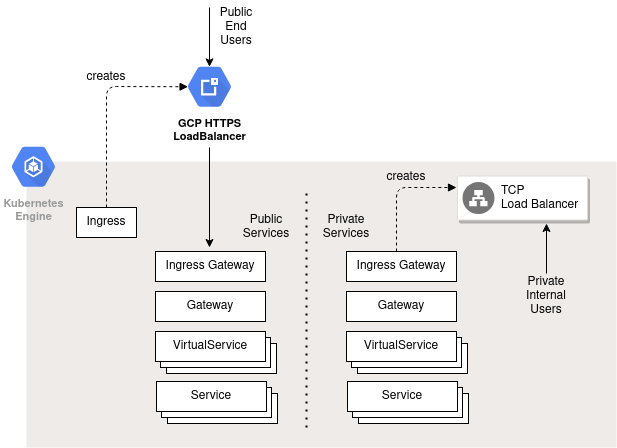
Internal TCP LB
In addition to the services being exposed to the public via the HTTPS LoadBalancer, we also created an internal TCP LoadBalancer.
The internal TCP LB is meant for internal services that, for example, should only be exposed to employees or those on the corporate Intranet. Example could be the Kubernetes dashboard, Prometheus web interface, or perhaps a custom Adm Web UI.
REFERENCES
google, exposing service mesh apps through gke ingress
ssorato, networking.gke.io/v1beta1.FrontendConfig: lb-http-to-https